A quick guide to Parameterized Queries
Parameterized queries in SQL are a critical concept that forms the backbone of secure and efficient database operations. These types of queries play a crucial role in preventing SQL injection attacks, and they also offer the advantage of improving performance through query plan reuse. Understanding parameterized queries is essential for anyone who interacts with relational databases.
What are parameterized queries?
SQL, or Structured Query Language, is the language we use to communicate with a database. We issue SQL commands to perform a range of tasks, from creating tables and inserting data to querying for specific information. When we want to retrieve specific data from a database, we often have to specify conditions - parameters - that the data must meet. For example, we might want to retrieve all orders made by a certain customer or all products within a certain price range.
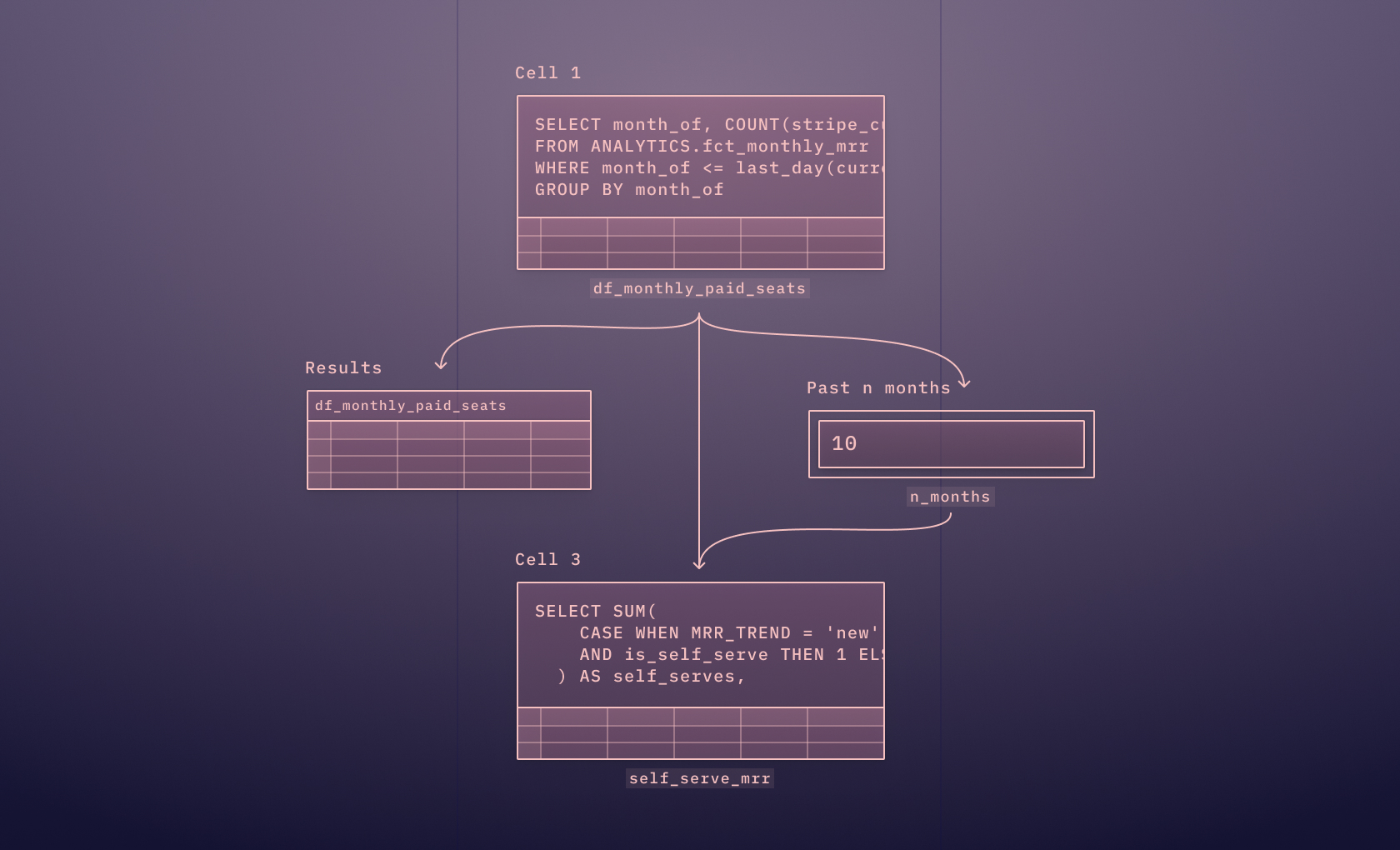
Here's where parameterized queries come into play. A parameterized query is a type of SQL query where placeholders are used for the parameters and the parameter values are supplied at execution time. They allow us to create a single query that can handle many different input values. For instance, instead of writing separate queries for each customer, we can write a single query and replace the customer ID with a placeholder.
Let's consider a simple example:
SELECT * FROM Customers WHERE CustomerID = @CustomerIDHere, @CustomerID is a placeholder that we can replace with an actual customer ID at runtime. The query's structure remains the same regardless of the specific customer we are interested in.
The benefits of parameterized queries
First, it prevents SQL injection attacks. SQL injection is a technique where an attacker manipulates the query by injecting malicious SQL code. By using placeholders, we are telling the database that the input should be treated as literal values, not part of the SQL command, mitigating this risk.
Second, it can improve performance. When SQL Server encounters a parameterized query, it compiles an execution plan that can be reused for different input values. This saves time, as the server doesn't have to compile a new plan every time the query is run with a different parameter.
Finally, it simplifies code and improves maintainability. Since we're writing less SQL code and the query's structure remains constant, our code becomes easier to manage and debug.
Parameterized queries are a fundamental SQL tool, offering a fusion of security, performance, and code efficiency. Understanding and effectively using them are essential skills in database management and development. By mastering parameterized queries, you're enhancing your ability to create robust, efficient, and secure applications.
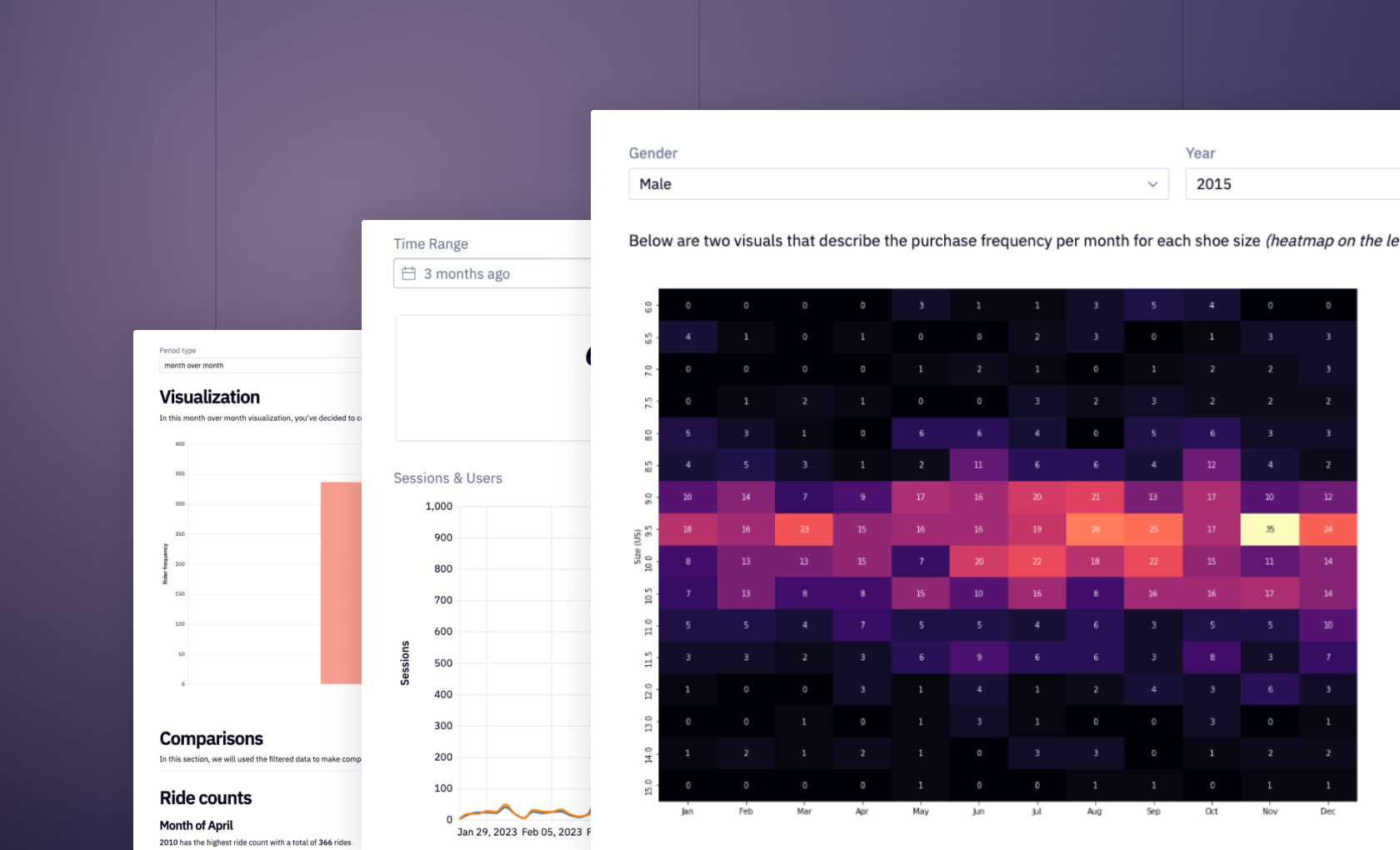
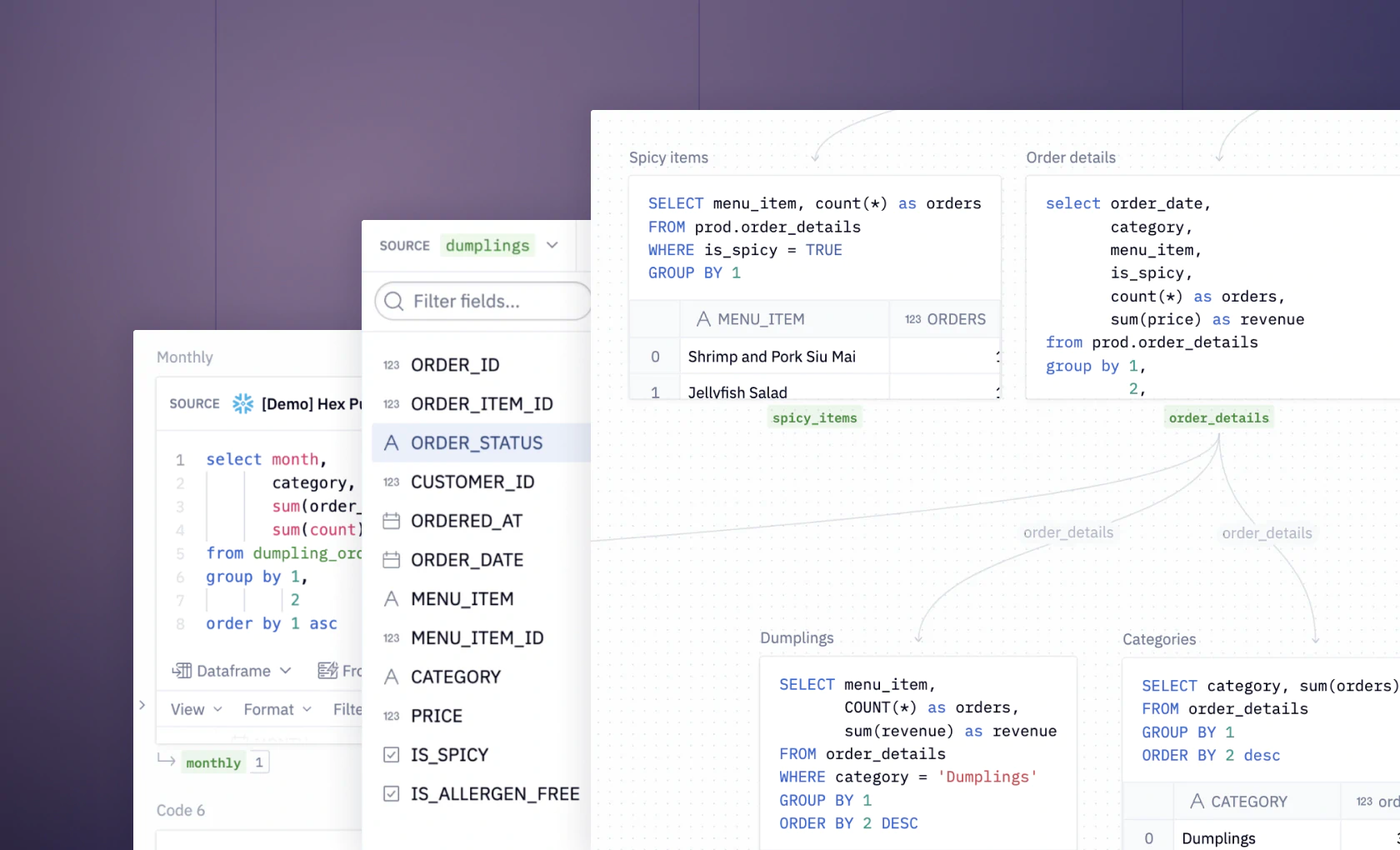
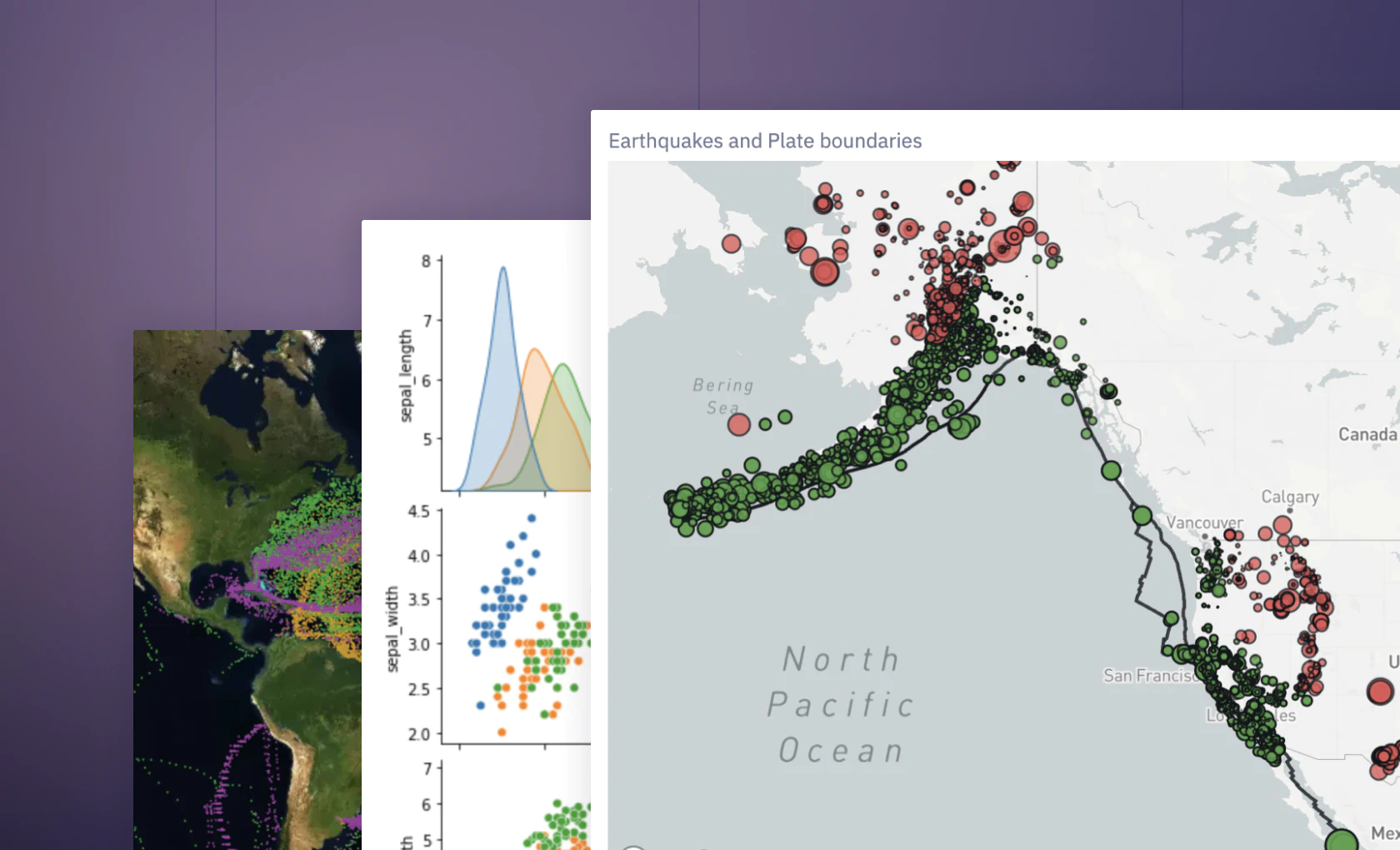
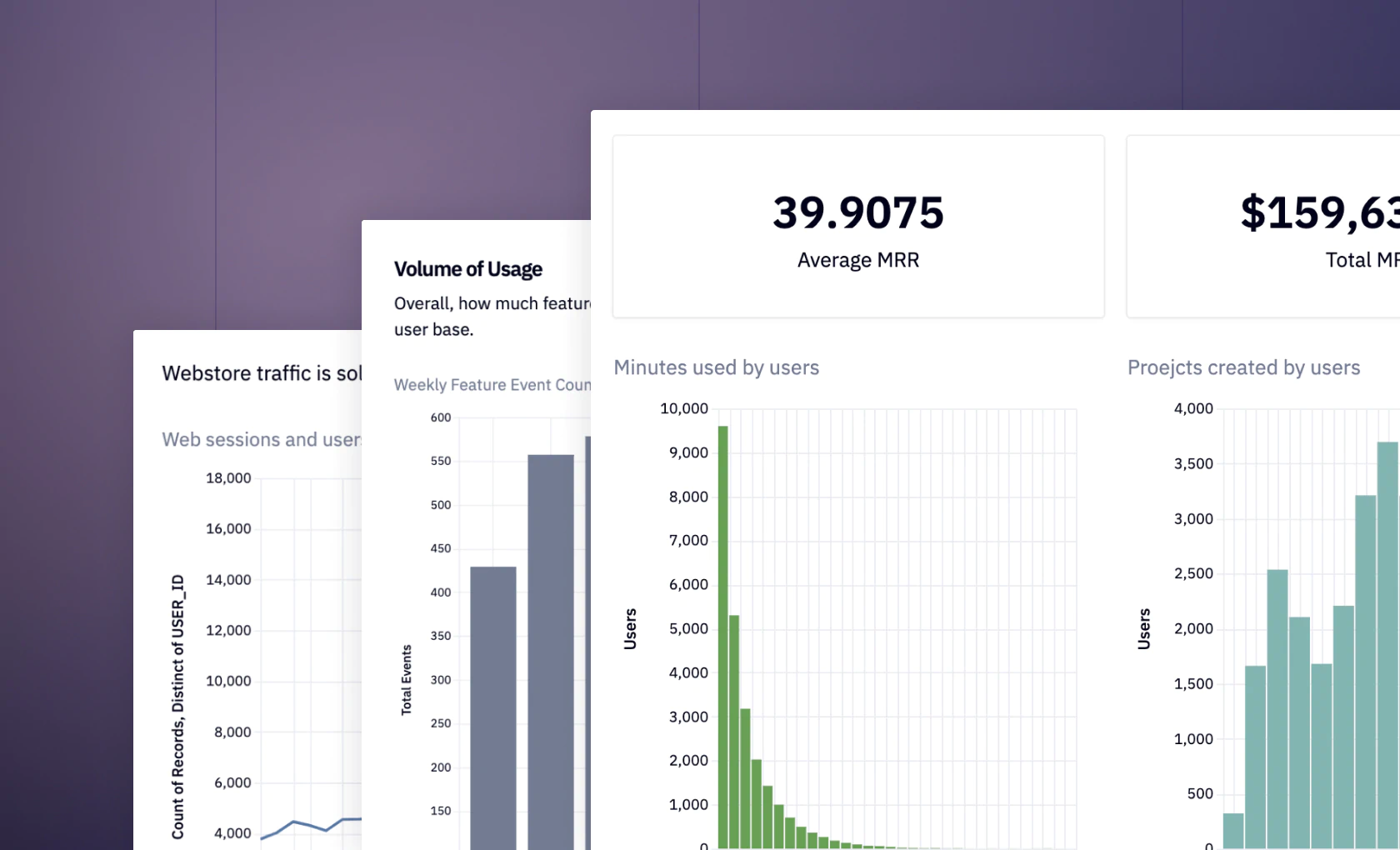
See what else Hex can do
Discover how other data scientists and analysts use Hex for everything from dashboards to deep dives.
FAQ
Yes, alternatives include using stored procedures, escaping all user-supplied input, or using ORM libraries which typically have built-in protection against SQL injection. However, parameterized queries are often the easiest and most effective way to prevent SQL injection attacks.
On the contrary, using parameterized queries can actually speed up your SQL queries. This is because the SQL server can often reuse the execution plan it creates for the query, reducing the resources required to run similar queries.
The limit varies depending on the SQL system. For example, SQL Server allows for a maximum of 2100 parameters in a single parameterized query.
Yes, SQL functions can work with parameterized queries. You can pass parameters to the function, which it can use in the query it executes.
No, SQL views are stored queries that represent a virtual table derived from one or more tables. They do not accept parameters. If you need to work with parameters, you should use a stored procedure or a table-valued function.
SQL Server uses a process called "parameter sniffing." When it receives a parameterized query, it creates an execution plan based on the parameter values. It then stores and reuses this plan for subsequent executions of the same query, even with different parameter values.
No special tools are required, but certain programming languages might require libraries to interact with databases using parameterized queries. For example, in Python, you would use a library like `psycopg2` for PostgreSQL or `pyodbc` for SQL Server.
Yes, you can use parameterized queries with the LIKE operator. However, remember that the placeholder replaces the entire string, including any wildcard characters, so those must be included with the parameter value itself.
While parameterized queries might require a bit more setup initially, they don't necessarily complicate the SQL code. The benefits of security, performance, and code maintainability often outweigh the initial setup effort.
Yes, you can use multiple parameters in a single parameterized query. This allows for complex queries where multiple conditions must be met, each with different input values.
No, parameterized queries and stored procedures are not the same. While both can use parameters, a stored procedure is a precompiled group of SQL statements stored in the database, which may or may not use parameterized queries as part of its code.
The concept of parameterized queries is common across various databases, but the exact implementation may vary. Most relational databases, including SQL Server, MySQL, PostgreSQL, and Oracle, support parameterized queries.
One drawback could be the extra development time initially required to set up parameterized queries. Also, if used incorrectly, they can lead to inefficient execution plans. However, the benefits in terms of security and performance often outweigh these considerations.
Yes, you can use parameterized queries for all types of SQL operations, including SELECT, INSERT, UPDATE, and DELETE. This allows for safer and more efficient manipulation of database data.
The actual values for parameters in a parameterized query are supplied at runtime. This can typically be done via your application code, where the placeholders in the SQL query are replaced with actual values before the query is run.
Yes, SQL Server can compile an execution plan for a parameterized query that can be reused for different input values. This can save time and resources as the server doesn't have to compile a new plan for every execution.
Parameterized queries treat input parameters as literal values, not part of the SQL command. This makes it impossible for an attacker to manipulate the query structure, effectively preventing SQL injection.
Parameterized queries are crucial for preventing SQL injection attacks and improving the performance of database operations. They also simplify the SQL code and enhance its maintainability.
A parameterized query in SQL is a query where placeholders are used for the parameters, and the actual parameter values are supplied at execution time. This allows us to create a single, reusable query for many different input values.
Can't find your answer here? Get in touch.